ADS - Alternate Data StreamsIf you're looking to hide files (text, exe, pics, etc..) here's a good place to teach you how. |
AirsnortAirSnort is a wireless LAN (WLAN) tool which cracks encryption keys on 802.11b WEP networks. AirSnort operates by passively monitoring transmissions, computing the encryption key when enough packets have been gathered. |
BFG / hydraBFG is a modified hydra tool, which now supports generating passwords in brute-force mode, unlike the original hydra. Of course, full source code is provided, and it should compile on all systems where hydra itself compiles, which means all UNIX-based systems including Linux, BSD, Mac OS, Windows (cygwin), etc. |
CPAN (Comprehensive Perl Archive Network)Here you will find All Things Perl: Perl modules Perl scripts Perl binary distributions ("ports") Perl source code Perl recent arrivals recent Perl modules |
Cheat Engine 5.4
 The coolest tool to hack all sorts of games, with powerful commands and friendly interface. Every game hacker must have this tool... * very useful also in browser games The coolest tool to hack all sorts of games, with powerful commands and friendly interface. Every game hacker must have this tool... * very useful also in browser games |
Cheat Engine 5.6Cheat Engine is an open source tool designed to help you with modifying single player games running under window so you can make them harder or easier depending on your preference(e.g: Find that 100hp is too easy, try playing a game with a max of 1 HP), but also contains other usefull tools to help debugging games and even normal applications. It comes with a memory scanner to quickly scan for variables used within a game and allow you to change them, but it also comes with a debugger, disassembler, assembler, speedhack, trainer maker, direct 3D manipulation tools, system inspection tools and more. |
ChickenfootChickenfoot is a Firefox extension that puts a programming environment in the browser's sidebar so you can write scripts to manipulate web pages and automate web browsing. |
Customize Your WebCustomize Your Web (CYW) let's you customize your favorite websites with just a few clicks. What Greasemonkey is for developers is CYW for non-developers. You can remove/rearrange /modify elements, add keyboard shortcuts and do many other things. Customization capabilities includes: * Removal and rearrangement of elements (cut / copy / paste behavior) * Modifying of elements in every possible way (changing size, color, default values ect.) * Definition of shortcuts / shortstrings for any clickable element * Keyboard navigation support for any list of elements (e.g. the result entries of search) * Insertion of arbitrary HTML and JavaScript code (of couse for this you need some programming knowledge) * Definition of small macros which are triggered by shortcut * Automatically triggering actions on page load (e.g. for automatic click on a login button or focusing a special field) |
DemocraKey
 DemocraKey It includes: * Tor Browser – For anonymous web browsing without using an insecure anonymous proxy * Clamwin Portable – To check the host computer for viruses, and to clean before surfing anonymously * Thunderbird Portable – Send anonymous email or encrypted email with Enigmail and GnuPGP * TrueCrypt – Create hidden volumes and encrypt your files so they are unreadable DemocraKey It includes: * Tor Browser – For anonymous web browsing without using an insecure anonymous proxy * Clamwin Portable – To check the host computer for viruses, and to clean before surfing anonymously * Thunderbird Portable – Send anonymous email or encrypted email with Enigmail and GnuPGP * TrueCrypt – Create hidden volumes and encrypt your files so they are unreadable |
Dev C++Bloodshed Dev-C++ is a full-featured Integrated Development Environment (IDE) for the C/C++ programming language. It uses Mingw port of GCC (GNU Compiler Collection) as it\'s compiler. Dev-C++ can also be used in combination with Cygwin or any other GCC based compiler. |
DollarDNS CrawlerThis tool allows one to recursively retrieve the result of any type of DNS record for all name servers a domain specifies |
DollarDNS WhoisDollarDNS Whois Direct allows users to make advanced WHOIS queries against a domain, including raw queries |
DownloadHelper
 "Using DownloadHelper, you can easily save videos from most of the popular video sites" -Main Site Lets you download videos from youtube, or almost any other video/music site in a flv format (that you can then convert after download) As simple as click and its downloaded! "Using DownloadHelper, you can easily save videos from most of the popular video sites" -Main Site Lets you download videos from youtube, or almost any other video/music site in a flv format (that you can then convert after download) As simple as click and its downloaded! |
FileZilla
 FileZilla ftp client FileZilla ftp client |
Firefox
 The most safe web browser for mac and windows. It has many types of add-ons, including hacking add-ons. The most safe web browser for mac and windows. It has many types of add-ons, including hacking add-ons. |
FirekeeperFirekeeper is an Intrusion Detection and Prevention System for Firefox. It is able to detect, block and warn the user about malicious sites. Firekeeper uses flexible rules similar to Snort ones to describe browser based attack attempts. Rules can also be used to effectively filter different kinds of unwanted content. |
Flasm
 A simple hacking tool for basic flash games. Change values (e.g. 999 lives) to increase fun! A simple hacking tool for basic flash games. Change values (e.g. 999 lives) to increase fun! |
GNU Emacs
 Due to it's extensibility it's a very useful tool editing code and miscellaneous. Also useful for general-purpose use. Due to it's extensibility it's a very useful tool editing code and miscellaneous. Also useful for general-purpose use. |
Geany
 Geany is a lightweight, fast, and compatible GTK2 based IDE. It supports many languages including but not limited to (PHP, C, C++, Ruby, Python, Bash). Geany is a lightweight, fast, and compatible GTK2 based IDE. It supports many languages including but not limited to (PHP, C, C++, Ruby, Python, Bash). |
Glype
 Glype proxy script is a free-to-use, web-based proxy script written in PHP. Similar to a typical proxy server, a web-proxy script downloads requested web pages and files and forwards them back to the user. The service is provided by a web page itself, which allows instant access to the proxy without editing your browser connection settings. Glype proxy script is a free-to-use, web-based proxy script written in PHP. Similar to a typical proxy server, a web-proxy script downloads requested web pages and files and forwards them back to the user. The service is provided by a web page itself, which allows instant access to the proxy without editing your browser connection settings. |
Google
 Google is your friend. Use it to the best of your ability. Don't misuse it. Don't be evil. Google is your friend. Use it to the best of your ability. Don't misuse it. Don't be evil. |
Google Hacks
 Google Hacks is a compilation of carefully crafted Google searches that expose novel functionality from Google\'s search and map services. For example, you can use it to view a timeline of your search results, view a map, search for music, search for books, and perform many other specific kinds of searches. You can also use this program to use google as a proxy. Google Hacks is a compilation of carefully crafted Google searches that expose novel functionality from Google\'s search and map services. For example, you can use it to view a timeline of your search results, view a map, search for music, search for books, and perform many other specific kinds of searches. You can also use this program to use google as a proxy. |
HackBar FireFox addon
 Simple security audit / Penetration test tool. This toolbar will help you in testing sql injections, XSS holes and site security. Simple security audit / Penetration test tool. This toolbar will help you in testing sql injections, XSS holes and site security. |
Hacking Vs. SecurityHacking Vs. Security is a hacking site, similar to HTS and HBH. It has simulated security challenges, an articles database, forum, etc. |
Hackman
 a Hex Editor, Disassembler and Template Creator/Editor. a Hex Editor, Disassembler and Template Creator/Editor. |
Hak5
 A website with some very interesting, informative videos. They cover wired and wireless networks, setting up a VoIP, way to many things to list here. You gotta check it out! A website with some very interesting, informative videos. They cover wired and wireless networks, setting up a VoIP, way to many things to list here. You gotta check it out! |
I2PI2P: Invisible Internet Project; I2P is an anonymizing network, offering a simple layer that identity-sensitive applications can use to securely communicate. All data is wrapped with several layers of encryption, and the network is both distributed and dynamic, with no trusted parties. Many applications are available that interface with I2P, including mail, peer-peer, IRC chat, and others. Can be seen as an alternative for the Tor Project. |
IPython
 An enhanced interactive shell for the python language, which includes object introspection. Excellent for experimenting with code and getting things to work. An enhanced interactive shell for the python language, which includes object introspection. Excellent for experimenting with code and getting things to work. |
Instructables
 Want to make an explosion or maybe something new for lunch. Instructions on almost anything at instructables.com Want to make an explosion or maybe something new for lunch. Instructions on almost anything at instructables.com |
Learn CPPA good site for learning C++. Gives you a C++ basis, teaches about variables, operators, even teaches you the history of C. |
LifeHacker.com
 An excellent tutorial, tips, and hacker's site with anything from finding the right timer application to triple-booting operating systems. Has sections for Mac, Linux, and Windows, and Android operating systems. An excellent tutorial, tips, and hacker's site with anything from finding the right timer application to triple-booting operating systems. Has sections for Mac, Linux, and Windows, and Android operating systems. |
Live Hacking CDLive Hacking CD is a new Linux distribution packed with tools and utilities for ethical hacking, penetration testing and countermeasure verification. Based on Ubuntu this ‘Live CD” runs directly from the CD and doesn’t require installation on your hard-drive. Once booted you can use the included tools to test, check, ethically hack and perform penetration tests on your own network to make sure that it is secure from outside intruders. |
Md5Decrypter.co.uk DatabaseOver 13 billion decrypted Md5 hashes. The largest Md5 database online. Crypt and decrypt you hashes. |
Medusa-GUI
 Graphical User Interface for the Medusa brute-forcing utility. Graphical User Interface for the Medusa brute-forcing utility. |
MiroVideo and music player that downloads torrents and converts files. Really useful. You can add websites directly to Miro like The Pirate Bay and Kickass torrents. Download them instantly. |
Netcat
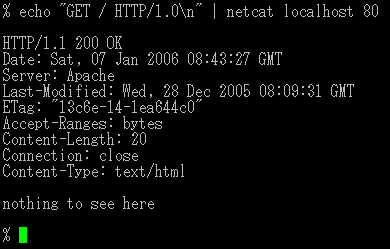 Netcat is a featured networking utility which reads and writes data across network connections, using the TCP/IP protocol. It is designed to be a reliable "back-end" tool that can be used directly or easily driven by other programs and scripts. At the same time, it is a feature-rich network debugging and exploration tool, since it can create almost any kind of connection you would need and has several interesting built-in capabilities. It provides access to the following main features: * Outbound and inbound connections, TCP or UDP, to or from any ports. * Featured tunneling mode which allows also special tunneling such as UDP to TCP, with the possibility of specifying all network parameters (source port/interface, listening port/interface, and the remote host allowed to connect to the tunnel. * Built-in port-scanning capabilities, with randomizer. * Advanced usage options, such as buffered send-mode (one line every N seconds), and hexdump (to stderr or to a specified file) of trasmitted and received data. * Optional RFC854 telnet codes parser and responder. Netcat is a featured networking utility which reads and writes data across network connections, using the TCP/IP protocol. It is designed to be a reliable "back-end" tool that can be used directly or easily driven by other programs and scripts. At the same time, it is a feature-rich network debugging and exploration tool, since it can create almost any kind of connection you would need and has several interesting built-in capabilities. It provides access to the following main features: * Outbound and inbound connections, TCP or UDP, to or from any ports. * Featured tunneling mode which allows also special tunneling such as UDP to TCP, with the possibility of specifying all network parameters (source port/interface, listening port/interface, and the remote host allowed to connect to the tunnel. * Built-in port-scanning capabilities, with randomizer. * Advanced usage options, such as buffered send-mode (one line every N seconds), and hexdump (to stderr or to a specified file) of trasmitted and received data. * Optional RFC854 telnet codes parser and responder. |
Nmap
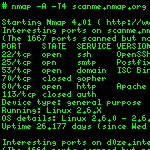 Nmap ("Network Mapper") is a free and open source (license) utility for network exploration or security auditing. Many systems and network administrators also find it useful for tasks such as network inventory, managing service upgrade schedules, and monitoring host or service uptime. Nmap uses raw IP packets in novel ways to determine what hosts are available on the network, what services (application name and version) those hosts are offering, what operating systems (and OS versions) they are running, what type of packet filters/firewalls are in use, and dozens of other characteristics. It was designed to rapidly scan large networks, but works fine against single hosts. Nmap runs on all major computer operating systems, and both console and graphical versions are available. Nmap ("Network Mapper") is a free and open source (license) utility for network exploration or security auditing. Many systems and network administrators also find it useful for tasks such as network inventory, managing service upgrade schedules, and monitoring host or service uptime. Nmap uses raw IP packets in novel ways to determine what hosts are available on the network, what services (application name and version) those hosts are offering, what operating systems (and OS versions) they are running, what type of packet filters/firewalls are in use, and dozens of other characteristics. It was designed to rapidly scan large networks, but works fine against single hosts. Nmap runs on all major computer operating systems, and both console and graphical versions are available. |
Nmap OnlineA web based implement of the popular port scanning utility, Nmap. |
Nmap/NmapFE(GUI)
 Nmap (\"Network Mapper\") is a free and open source (license) utility for network exploration or security auditing. Many systems and network administrators also find it useful for tasks such as network inventory, managing service upgrade schedules, and monitoring host or service uptime. Nmap uses raw IP packets in novel ways to determine what hosts are available on the network, what services (application name and version) those hosts are offering, what operating systems (and OS versions) they are running, what type of packet filters/firewalls are in use, and dozens of other characteristics. It was designed to rapidly scan large networks, but works fine against single hosts. Nmap runs on all major computer operating systems, and both console and graphical versions are available. Nmap (\"Network Mapper\") is a free and open source (license) utility for network exploration or security auditing. Many systems and network administrators also find it useful for tasks such as network inventory, managing service upgrade schedules, and monitoring host or service uptime. Nmap uses raw IP packets in novel ways to determine what hosts are available on the network, what services (application name and version) those hosts are offering, what operating systems (and OS versions) they are running, what type of packet filters/firewalls are in use, and dozens of other characteristics. It was designed to rapidly scan large networks, but works fine against single hosts. Nmap runs on all major computer operating systems, and both console and graphical versions are available. |
OWASP
 Web security wiki - lots and lots of detailed articles on different attacks and how to prevent them. Web security wiki - lots and lots of detailed articles on different attacks and how to prevent them. |
OWASP Web application Testing guide
 The OWASP Testing Guide includes a "best practice" penetration testing framework which users can implement in their own organizations and a "low level" penetration testing guide that describes techniques for testing most common web application and web service security issues. The OWASP Testing Guide includes a "best practice" penetration testing framework which users can implement in their own organizations and a "low level" penetration testing guide that describes techniques for testing most common web application and web service security issues. |
Okteta
 Okteta is a simple editor for the raw data of files. This type of program is also called hex editor or binary editor. Now that KDE is cross platform, this program can not only be used on Linux, but on Windows and MacOSx as well! Okteta is a simple editor for the raw data of files. This type of program is also called hex editor or binary editor. Now that KDE is cross platform, this program can not only be used on Linux, but on Windows and MacOSx as well! |
OldschoolphreakGood information on phone hacking and other methods. |
OperaOpera is a fast and secure web browser that features pop-up blocking, tabbed browsing, integrated searches, RSS, e-mail, and even IRC chat. A wide variety of add-ons ("widgets") are available from games, instant messaging, file sharing, media players, page source editor, cookie editor etc. Why Opera?(by the author) Speed up your surfing: Get the fastest JavaScript engine ever Browse more quickly on slow connections See smooth animations and super-fast graphics Make the most of your mouse ake the Web easier: Search right from the address field Find your way back with a smart address field Get suggestions as you search Use any search engine from the browser Quickly find what you need in any page Multitask effectively with flexible tabs Get a quick look inside your tabs Get a better view of open webpages Keep your spelling in check Make reading easier on the eyes Access favorite websites with one click Have your data wherever you need it Do more with unique Powerful features: Stay in control of your downloads (Support for BitTorrent is also included) Eliminate distractions with content blocking Email with a powerful, efficient mail client Customization: Select from hundreds of skins Use convenient and entertaining widgets Share and remotely access files, music and photos Peace of mind: Rest assured with Opera's Web Threat Protection and Extended Validation Keep an eye on security Browse without leaving a trace Stay up to date automatically Control your cookies Developer support: Enjoy support for the latest standards(HTML5,CSS3) Debug complex websites with Opera Dragonfly Know where you are with Geolocation |
OphcrackA Windows or other OS'es such as Mac or Linux hacking utility for hacking logon passwords. |
PHP.net
 PHP is a widely-used general-purpose scripting language that is especially suited for Web development and can be embedded into HTML. If you are new to PHP and want to get some idea of how it works, try the introductory tutorial. After that, check out the online manual, and the example archive sites and some of the other resources available in the links section. PHP is a widely-used general-purpose scripting language that is especially suited for Web development and can be embedded into HTML. If you are new to PHP and want to get some idea of how it works, try the introductory tutorial. After that, check out the online manual, and the example archive sites and some of the other resources available in the links section. |
Peer GuardianPeer Guardian is Phoenix Labs’ premier IP blocker. Peer Guardian integrates support for multiple lists, list editing, automatic updates, and blocking all of IPv4 (TCP, UDP, ICMP, etc), making it the safest and easiest way to protect your privacy on P2P. It currently has a Windows, Linux, Lite, and OSX version. It blocks Government, Anti-P2P, Education, Virus, Spyware, and other I.P.s. This is a highly recommended tool. It also supports your own custom block list of I.P.s. |
PerlPerl is a highly capable, feature-rich programming language with over 22 years of development. Perl Features : Powerful, stable, mature, portable. Mission critical. High Quality Code. Object-oriented, procedural and functional. Easily extendible. Text manipulation. Unicode support. Database integration. C/C++ library interface. Embeddable. Open Source. Ideal web programming language. Web Frameworks. Database integration. Web modules(CPAN). Duct-tape of the internet, and more... Encryption capable. Embed into Apache. |
Phreaks and GeeksGood information on Phreaking and phone hacking. |
Physics IllustratorA motion simulator for the Tablet PC that demonstrates physics by using objects that are drawn by the user. |
Plain-text.infohuge database of Online Rainbow Tables |
Portable AppsPortableApps.com provides a truly open platform that works with any hardware you like (USB flash drive, iPod, portable hard drive, etc). The entire platform is open source built around an open format that any hardware or software provider can use. |
Product Key FinderWith the award-winning Product Key Finder, you can instantly find product key and serial number from currently installed Windows, Office, SQL Server, Exchange Server and many other products. Product Key Finder enables you to retrieve your Windows 2000, 2003, NT, or XP product key, even if you cann't boot your computer into Windows! No other product can... By The Death Adder |
Programmer's NotepadThis is an all- around must for a programmer. This is a code editor/creator/conve rter for many of the common programming languages. From FORTRAN to Ruby, Python, and C++. Enjoy and use often. |
RefControlA Firefox addon to control what gets sent as the HTTP Referer on a per-site basis. |
Remote Exploit's Backtrack 3
 This is a VERY useful Linux Slax live CD developed for Penetration Testing. All you need to do is burn the .iso image to a CD and boot to it after a restart on any computer. BT3 has a NICE collection of tools that can be used for hacking, windows password cracking,network mapping, and a bunch of other fun tools to mess around with. It also has KDE and Flux, so it has a very friendly GUI. Check it out! This is a VERY useful Linux Slax live CD developed for Penetration Testing. All you need to do is burn the .iso image to a CD and boot to it after a restart on any computer. BT3 has a NICE collection of tools that can be used for hacking, windows password cracking,network mapping, and a bunch of other fun tools to mess around with. It also has KDE and Flux, so it has a very friendly GUI. Check it out! |
Request Policy
 RequestPolicy is an extension for Mozilla browsers that improves the privacy and security of your browsing by giving you control over when cross-site requests are allowed by webpages you visit. It is the first comprehensive client-side protection against CSRF attacks and the first tool to enable the use of modern browsers without cross-site information leakage. It is compatible with Firefox 3+, SeaMonkey 2.0, Flock 2.0, Songbird 1.0, and Fennec 1.0. It works wherever these browsers do (Linux, BSD, Mac, Windows, etc.). RequestPolicy is an extension for Mozilla browsers that improves the privacy and security of your browsing by giving you control over when cross-site requests are allowed by webpages you visit. It is the first comprehensive client-side protection against CSRF attacks and the first tool to enable the use of modern browsers without cross-site information leakage. It is compatible with Firefox 3+, SeaMonkey 2.0, Flock 2.0, Songbird 1.0, and Fennec 1.0. It works wherever these browsers do (Linux, BSD, Mac, Windows, etc.). |
Ruby
 A dynamic, open source programming language with a focus on simplicity and productivity. It has an elegant syntax that is natural to read and easy to write. A dynamic, open source programming language with a focus on simplicity and productivity. It has an elegant syntax that is natural to read and easy to write. |
SCGMD3The super crazy guitar maniac returns with 14 new songs to master and 10 awesome guitars to choose from! (13+) (You can download this game onto a jump drive, and stick it into any school comp to play it. It doesn't require the browser, so it will not be blocked.) JUST DONT GET INTO TROUBLE WITH IT!! |
SECDOCS
 Somewhat similar to milw0rm (RIP): documentation related to hacking/security Somewhat similar to milw0rm (RIP): documentation related to hacking/security |
SUPERAntiSpyware
 Finds and removes spyware, adware, malware, keyloggers, trojans, and rootkits. Finds and removes spyware, adware, malware, keyloggers, trojans, and rootkits. |
Slave HackA (sometimes) realistic computer hacking game, it allows you to crack in a simulated environment against real people from around the world |
Slave hackA (sometimes) realistic computer hacking game, it allows you to crack in a simulated environment against real people from around the world. Old slave hack link not working. |
Snort
 SNORT® is an open source network intrusion prevention and detection system utilizing a rule-driven language, which combines the benefits of signature, protocol and anomaly based inspection methods. With millions of downloads to date, Snort is the most widely deployed intrusion detection and prevention technology worldwide and has become the de facto standard for the industry. SNORT® is an open source network intrusion prevention and detection system utilizing a rule-driven language, which combines the benefits of signature, protocol and anomaly based inspection methods. With millions of downloads to date, Snort is the most widely deployed intrusion detection and prevention technology worldwide and has become the de facto standard for the industry. |
SnortSam
 SnortSam is a plugin for Snort, an open-source light-weight Intrusion Detection System (IDS). The plugin allows for automated blocking of IP addresses on several firewalls. SnortSam is a plugin for Snort, an open-source light-weight Intrusion Detection System (IDS). The plugin allows for automated blocking of IP addresses on several firewalls. |
T E X T F I L E S
 Lots on info and articles that's been compiled over the years...many topics...worth reading Lots on info and articles that's been compiled over the years...many topics...worth reading |
T-SearchT-Search is a program that lets you search for values that are stored or downloaded into memory. This program, is usually used to hack games! |
Teach yourself web designA Directory of free online courses and learning tools. Everything you need to become a Web designer. |
Tizag
 Tizag was designed to teach beginner web programmers how to use HTML and CSS. We invite you to begin the tutorials right away. We have... * A Beginner tutorial - For those just starting to learn to make web pages. * HTML Tutorial - Begin your web designing with a solid background in HTML. * CSS Tutorial - Check out the latest web design techniques available to you. * PHP Tutorial - Understand what all the PHP hype is about with our tutorial. * Web Host Guide - An overview of all the information you need to know about choosing and using a web host. * CSS Reference - CSS Quick-Reference sheet. Each item of the reference also has an accompanying example. * HTML Reference - HTML Tag Reference including attributes associated with each tag and accompanying examples. Tizag was designed to teach beginner web programmers how to use HTML and CSS. We invite you to begin the tutorials right away. We have... * A Beginner tutorial - For those just starting to learn to make web pages. * HTML Tutorial - Begin your web designing with a solid background in HTML. * CSS Tutorial - Check out the latest web design techniques available to you. * PHP Tutorial - Understand what all the PHP hype is about with our tutorial. * Web Host Guide - An overview of all the information you need to know about choosing and using a web host. * CSS Reference - CSS Quick-Reference sheet. Each item of the reference also has an accompanying example. * HTML Reference - HTML Tag Reference including attributes associated with each tag and accompanying examples. |
Tuts 4 You
 This site is dedicated to all the researchers and reverse engineers interested in Reverse Code Engineering (RCE) techniques and practices and all things related. You will be able to find a wide breadth of information retained on this site to help in your research ranging from; anti-debugging, virtual machines, unpacking, coding, disassembling, debugging, keygenning, cryptography and much, much more. This site is dedicated to all the researchers and reverse engineers interested in Reverse Code Engineering (RCE) techniques and practices and all things related. You will be able to find a wide breadth of information retained on this site to help in your research ranging from; anti-debugging, virtual machines, unpacking, coding, disassembling, debugging, keygenning, cryptography and much, much more. |
Unity 3s a game development tool that has been designed to let you focus on creating amazing games. over 500,000 game and private game producer use it so hey it must be good, why don,t you check it out. |
VIM
 Vim is a highly configurable text editor built to enable efficient text editing. It is an improved version of the vi editor distributed with most UNIX systems. Vim is often called a "programmer's editor," and so useful for programming that many consider it an entire IDE. It's not just for programmers, though. Vim is perfect for all kinds of text editing, from composing email to editing configuration files. Vim is a highly configurable text editor built to enable efficient text editing. It is an improved version of the vi editor distributed with most UNIX systems. Vim is often called a "programmer's editor," and so useful for programming that many consider it an entire IDE. It's not just for programmers, though. Vim is perfect for all kinds of text editing, from composing email to editing configuration files. |
VirtualBoxVirtualBox is a free general-purpose full virtualizer for x86 hardware. Targeted at server, desktop and embedded use, it is now the only professional-quality virtualization solution that is also Open Source Software. |
Visual IRCIt is a FREE IRC client that is very good and so far error free. PLus has various ways to customize things. |
W3Schools
 At W3Schools you will find all the Web-building tutorials you need, from basic HTML and XHTML to advanced XML, SQL, Database, Multimedia and WAP, Totally Free. Great for people new to computer languages. At W3Schools you will find all the Web-building tutorials you need, from basic HTML and XHTML to advanced XML, SQL, Database, Multimedia and WAP, Totally Free. Great for people new to computer languages. |
W3af
 Web Application Attack and Audit Framework. W3af is a great piece of software designed for testing web applications. Written in Python. Comes with over 100 plugins for brute-forcing, evasion, page discovery, exploit discovery and exploits. Extensible with Python. Web Application Attack and Audit Framework. W3af is a great piece of software designed for testing web applications. Written in Python. Comes with over 100 plugins for brute-forcing, evasion, page discovery, exploit discovery and exploits. Extensible with Python. |
Web Developer [Toolbar]Firefox add-on. This toolbar allows you to edit and view parts of a webpage in a user-friendly way, even when they are not normally so obvious. (Great for HTS) |
Webgoat
 WebGoat is a deliberately insecure J2EE web application maintained by OWASP designed to teach web application security lessons. In each lesson, users must demonstrate their understanding of a security issue by exploiting a real vulnerability in the WebGoat application. For example, in one of the lessons the user must use SQL injection to steal fake credit card numbers. The application is a realistic teaching environment, providing users with hints and code to further explain the lesson. WebGoat is a deliberately insecure J2EE web application maintained by OWASP designed to teach web application security lessons. In each lesson, users must demonstrate their understanding of a security issue by exploiting a real vulnerability in the WebGoat application. For example, in one of the lessons the user must use SQL injection to steal fake credit card numbers. The application is a realistic teaching environment, providing users with hints and code to further explain the lesson. |
WhatWeb
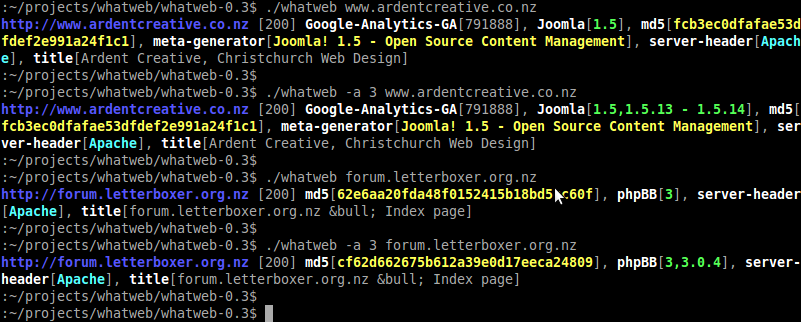 WhatWeb is a next generation web scanner that identifies what websites are running. Flexible plugin architecture with over 80 plugins so far. Passive plugins use information in the headers, cookies, HTML body and URL. Aggressive plugins can identify versions of Joomla, phpBB, etc by making extra requests to the webserver WhatWeb is a next generation web scanner that identifies what websites are running. Flexible plugin architecture with over 80 plugins so far. Passive plugins use information in the headers, cookies, HTML body and URL. Aggressive plugins can identify versions of Joomla, phpBB, etc by making extra requests to the webserver |
Win SCPsftp client |
XVI32
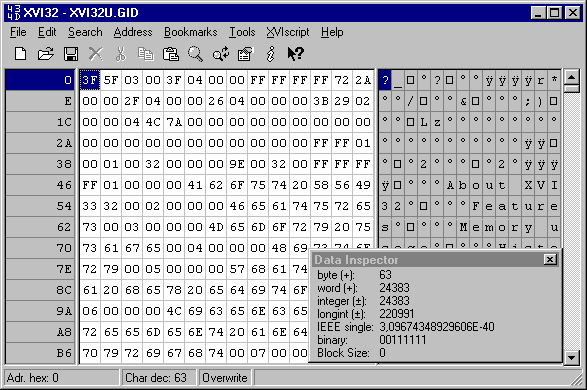 XVI32 is a freeware hex editor running under Windows 95, Windows 98, Windows NT, Windows 2000, and Windows XP. XVI32 is a freeware hex editor running under Windows 95, Windows 98, Windows NT, Windows 2000, and Windows XP. |
bmp2tabBitmap to Html table convertor: This little tool pushes your browser to it's limits! It will convert a bitmap file to a HTML table. This way it's possible to create a scalable image which cannot be saved as an image! |
distrowatchYeah, Find the distro you want :) |
iMacroFirefox add-on. Records what you do then repeats as many times as you want |
ophcrackOphcrack is a free Windows password cracker based on rainbow tables. It is a very efficient implementation of rainbow tables done by the inventors of the method. It comes with a Graphical User Interface and runs on multiple platforms. Features: * » Runs on Windows, Linux/Unix, Mac OS X, ... * » Cracks LM and NTLM hashes. * » Free tables available for Windows XP and Vista. * » Brute-force module for simple passwords. * » LiveCD available to simplify the cracking. * » Loads hashes from encrypted SAM recovered from a Windows partition, Vista included. * » Free and open source software (GPL). |
socatsocat is a relay for bidirectional data transfer between two independent data channels. Each of these data channels may be a file, pipe, device (serial line etc. or a pseudo terminal), a socket (UNIX, IP4, IP6 - raw, UDP, TCP), an SSL socket, proxy CONNECT connection, a file descriptor (stdin etc.), the GNU line editor (readline), a program, or a combination of two of these. These modes include generation of "listening" sockets, named pipes, and pseudo terminals. tl;dr a better netcat with more capability |
tlbox (tool box)
 This site offers a collection of tutorials, articles, and programs useful for people interested in programing, system administration, and web design for Windows, Mac, or Linux. This site offers a collection of tutorials, articles, and programs useful for people interested in programing, system administration, and web design for Windows, Mac, or Linux. |








 The coolest tool to hack all sorts of games, with powerful commands and friendly interface. Every game hacker must have this tool... * very useful also in browser games
The coolest tool to hack all sorts of games, with powerful commands and friendly interface. Every game hacker must have this tool... * very useful also in browser games DemocraKey It includes: * Tor Browser – For anonymous web browsing without using an insecure anonymous proxy * Clamwin Portable – To check the host computer for viruses, and to clean before surfing anonymously * Thunderbird Portable – Send anonymous email or encrypted email with Enigmail and GnuPGP * TrueCrypt – Create hidden volumes and encrypt your files so they are unreadable
DemocraKey It includes: * Tor Browser – For anonymous web browsing without using an insecure anonymous proxy * Clamwin Portable – To check the host computer for viruses, and to clean before surfing anonymously * Thunderbird Portable – Send anonymous email or encrypted email with Enigmail and GnuPGP * TrueCrypt – Create hidden volumes and encrypt your files so they are unreadable "Using DownloadHelper, you can easily save videos from most of the popular video sites" -Main Site Lets you download videos from youtube, or almost any other video/music site in a flv format (that you can then convert after download) As simple as click and its downloaded!
"Using DownloadHelper, you can easily save videos from most of the popular video sites" -Main Site Lets you download videos from youtube, or almost any other video/music site in a flv format (that you can then convert after download) As simple as click and its downloaded! FileZilla ftp client
FileZilla ftp client The most safe web browser for mac and windows. It has many types of add-ons, including hacking add-ons.
The most safe web browser for mac and windows. It has many types of add-ons, including hacking add-ons. Due to it's extensibility it's a very useful tool editing code and miscellaneous. Also useful for general-purpose use.
Due to it's extensibility it's a very useful tool editing code and miscellaneous. Also useful for general-purpose use. Geany is a lightweight, fast, and compatible GTK2 based IDE. It supports many languages including but not limited to (PHP, C, C++, Ruby, Python, Bash).
Geany is a lightweight, fast, and compatible GTK2 based IDE. It supports many languages including but not limited to (PHP, C, C++, Ruby, Python, Bash). Glype proxy script is a free-to-use, web-based proxy script written in PHP. Similar to a typical proxy server, a web-proxy script downloads requested web pages and files and forwards them back to the user. The service is provided by a web page itself, which allows instant access to the proxy without editing your browser connection settings.
Glype proxy script is a free-to-use, web-based proxy script written in PHP. Similar to a typical proxy server, a web-proxy script downloads requested web pages and files and forwards them back to the user. The service is provided by a web page itself, which allows instant access to the proxy without editing your browser connection settings. Google is your friend. Use it to the best of your ability. Don't misuse it. Don't be evil.
Google is your friend. Use it to the best of your ability. Don't misuse it. Don't be evil. Google Hacks is a compilation of carefully crafted Google searches that expose novel functionality from Google\'s search and map services. For example, you can use it to view a timeline of your search results, view a map, search for music, search for books, and perform many other specific kinds of searches. You can also use this program to use google as a proxy.
Google Hacks is a compilation of carefully crafted Google searches that expose novel functionality from Google\'s search and map services. For example, you can use it to view a timeline of your search results, view a map, search for music, search for books, and perform many other specific kinds of searches. You can also use this program to use google as a proxy. a Hex Editor, Disassembler and Template Creator/Editor.
a Hex Editor, Disassembler and Template Creator/Editor. A website with some very interesting, informative videos. They cover wired and wireless networks, setting up a VoIP, way to many things to list here. You gotta check it out!
A website with some very interesting, informative videos. They cover wired and wireless networks, setting up a VoIP, way to many things to list here. You gotta check it out! Want to make an explosion or maybe something new for lunch. Instructions on almost anything at instructables.com
Want to make an explosion or maybe something new for lunch. Instructions on almost anything at instructables.com An excellent tutorial, tips, and hacker's site with anything from finding the right timer application to triple-booting operating systems. Has sections for Mac, Linux, and Windows, and Android operating systems.
An excellent tutorial, tips, and hacker's site with anything from finding the right timer application to triple-booting operating systems. Has sections for Mac, Linux, and Windows, and Android operating systems. Netcat is a featured networking utility which reads and writes data across network connections, using the TCP/IP protocol. It is designed to be a reliable "back-end" tool that can be used directly or easily driven by other programs and scripts. At the same time, it is a feature-rich network debugging and exploration tool, since it can create almost any kind of connection you would need and has several interesting built-in capabilities. It provides access to the following main features: * Outbound and inbound connections, TCP or UDP, to or from any ports. * Featured tunneling mode which allows also special tunneling such as UDP to TCP, with the possibility of specifying all network parameters (source port/interface, listening port/interface, and the remote host allowed to connect to the tunnel. * Built-in port-scanning capabilities, with randomizer. * Advanced usage options, such as buffered send-mode (one line every N seconds), and hexdump (to stderr or to a specified file) of trasmitted and received data. * Optional RFC854 telnet codes parser and responder.
Netcat is a featured networking utility which reads and writes data across network connections, using the TCP/IP protocol. It is designed to be a reliable "back-end" tool that can be used directly or easily driven by other programs and scripts. At the same time, it is a feature-rich network debugging and exploration tool, since it can create almost any kind of connection you would need and has several interesting built-in capabilities. It provides access to the following main features: * Outbound and inbound connections, TCP or UDP, to or from any ports. * Featured tunneling mode which allows also special tunneling such as UDP to TCP, with the possibility of specifying all network parameters (source port/interface, listening port/interface, and the remote host allowed to connect to the tunnel. * Built-in port-scanning capabilities, with randomizer. * Advanced usage options, such as buffered send-mode (one line every N seconds), and hexdump (to stderr or to a specified file) of trasmitted and received data. * Optional RFC854 telnet codes parser and responder. Nmap ("Network Mapper") is a free and open source (license) utility for network exploration or security auditing. Many systems and network administrators also find it useful for tasks such as network inventory, managing service upgrade schedules, and monitoring host or service uptime. Nmap uses raw IP packets in novel ways to determine what hosts are available on the network, what services (application name and version) those hosts are offering, what operating systems (and OS versions) they are running, what type of packet filters/firewalls are in use, and dozens of other characteristics. It was designed to rapidly scan large networks, but works fine against single hosts. Nmap runs on all major computer operating systems, and both console and graphical versions are available.
Nmap ("Network Mapper") is a free and open source (license) utility for network exploration or security auditing. Many systems and network administrators also find it useful for tasks such as network inventory, managing service upgrade schedules, and monitoring host or service uptime. Nmap uses raw IP packets in novel ways to determine what hosts are available on the network, what services (application name and version) those hosts are offering, what operating systems (and OS versions) they are running, what type of packet filters/firewalls are in use, and dozens of other characteristics. It was designed to rapidly scan large networks, but works fine against single hosts. Nmap runs on all major computer operating systems, and both console and graphical versions are available. Nmap (\"Network Mapper\") is a free and open source (license) utility for network exploration or security auditing. Many systems and network administrators also find it useful for tasks such as network inventory, managing service upgrade schedules, and monitoring host or service uptime. Nmap uses raw IP packets in novel ways to determine what hosts are available on the network, what services (application name and version) those hosts are offering, what operating systems (and OS versions) they are running, what type of packet filters/firewalls are in use, and dozens of other characteristics. It was designed to rapidly scan large networks, but works fine against single hosts. Nmap runs on all major computer operating systems, and both console and graphical versions are available.
Nmap (\"Network Mapper\") is a free and open source (license) utility for network exploration or security auditing. Many systems and network administrators also find it useful for tasks such as network inventory, managing service upgrade schedules, and monitoring host or service uptime. Nmap uses raw IP packets in novel ways to determine what hosts are available on the network, what services (application name and version) those hosts are offering, what operating systems (and OS versions) they are running, what type of packet filters/firewalls are in use, and dozens of other characteristics. It was designed to rapidly scan large networks, but works fine against single hosts. Nmap runs on all major computer operating systems, and both console and graphical versions are available. Web security wiki - lots and lots of detailed articles on different attacks and how to prevent them.
Web security wiki - lots and lots of detailed articles on different attacks and how to prevent them. The OWASP Testing Guide includes a "best practice" penetration testing framework which users can implement in their own organizations and a "low level" penetration testing guide that describes techniques for testing most common web application and web service security issues.
The OWASP Testing Guide includes a "best practice" penetration testing framework which users can implement in their own organizations and a "low level" penetration testing guide that describes techniques for testing most common web application and web service security issues. Okteta is a simple editor for the raw data of files. This type of program is also called hex editor or binary editor. Now that KDE is cross platform, this program can not only be used on Linux, but on Windows and MacOSx as well!
Okteta is a simple editor for the raw data of files. This type of program is also called hex editor or binary editor. Now that KDE is cross platform, this program can not only be used on Linux, but on Windows and MacOSx as well! PHP is a widely-used general-purpose scripting language that is especially suited for Web development and can be embedded into HTML. If you are new to PHP and want to get some idea of how it works, try the introductory tutorial. After that, check out the online manual, and the example archive sites and some of the other resources available in the links section.
PHP is a widely-used general-purpose scripting language that is especially suited for Web development and can be embedded into HTML. If you are new to PHP and want to get some idea of how it works, try the introductory tutorial. After that, check out the online manual, and the example archive sites and some of the other resources available in the links section. This is a VERY useful Linux Slax live CD developed for Penetration Testing. All you need to do is burn the .iso image to a CD and boot to it after a restart on any computer. BT3 has a NICE collection of tools that can be used for hacking, windows password cracking,network mapping, and a bunch of other fun tools to mess around with. It also has KDE and Flux, so it has a very friendly GUI. Check it out!
This is a VERY useful Linux Slax live CD developed for Penetration Testing. All you need to do is burn the .iso image to a CD and boot to it after a restart on any computer. BT3 has a NICE collection of tools that can be used for hacking, windows password cracking,network mapping, and a bunch of other fun tools to mess around with. It also has KDE and Flux, so it has a very friendly GUI. Check it out! RequestPolicy is an extension for Mozilla browsers that improves the privacy and security of your browsing by giving you control over when cross-site requests are allowed by webpages you visit. It is the first comprehensive client-side protection against CSRF attacks and the first tool to enable the use of modern browsers without cross-site information leakage. It is compatible with Firefox 3+, SeaMonkey 2.0, Flock 2.0, Songbird 1.0, and Fennec 1.0. It works wherever these browsers do (Linux, BSD, Mac, Windows, etc.).
RequestPolicy is an extension for Mozilla browsers that improves the privacy and security of your browsing by giving you control over when cross-site requests are allowed by webpages you visit. It is the first comprehensive client-side protection against CSRF attacks and the first tool to enable the use of modern browsers without cross-site information leakage. It is compatible with Firefox 3+, SeaMonkey 2.0, Flock 2.0, Songbird 1.0, and Fennec 1.0. It works wherever these browsers do (Linux, BSD, Mac, Windows, etc.). A dynamic, open source programming language with a focus on simplicity and productivity. It has an elegant syntax that is natural to read and easy to write.
A dynamic, open source programming language with a focus on simplicity and productivity. It has an elegant syntax that is natural to read and easy to write. Somewhat similar to milw0rm (RIP): documentation related to hacking/security
Somewhat similar to milw0rm (RIP): documentation related to hacking/security Finds and removes spyware, adware, malware, keyloggers, trojans, and rootkits.
Finds and removes spyware, adware, malware, keyloggers, trojans, and rootkits. SNORT® is an open source network intrusion prevention and detection system utilizing a rule-driven language, which combines the benefits of signature, protocol and anomaly based inspection methods. With millions of downloads to date, Snort is the most widely deployed intrusion detection and prevention technology worldwide and has become the de facto standard for the industry.
SNORT® is an open source network intrusion prevention and detection system utilizing a rule-driven language, which combines the benefits of signature, protocol and anomaly based inspection methods. With millions of downloads to date, Snort is the most widely deployed intrusion detection and prevention technology worldwide and has become the de facto standard for the industry. SnortSam is a plugin for Snort, an open-source light-weight Intrusion Detection System (IDS). The plugin allows for automated blocking of IP addresses on several firewalls.
SnortSam is a plugin for Snort, an open-source light-weight Intrusion Detection System (IDS). The plugin allows for automated blocking of IP addresses on several firewalls. Lots on info and articles that's been compiled over the years...many topics...worth reading
Lots on info and articles that's been compiled over the years...many topics...worth reading Tizag was designed to teach beginner web programmers how to use HTML and CSS. We invite you to begin the tutorials right away. We have... * A Beginner tutorial - For those just starting to learn to make web pages. * HTML Tutorial - Begin your web designing with a solid background in HTML. * CSS Tutorial - Check out the latest web design techniques available to you. * PHP Tutorial - Understand what all the PHP hype is about with our tutorial. * Web Host Guide - An overview of all the information you need to know about choosing and using a web host. * CSS Reference - CSS Quick-Reference sheet. Each item of the reference also has an accompanying example. * HTML Reference - HTML Tag Reference including attributes associated with each tag and accompanying examples.
Tizag was designed to teach beginner web programmers how to use HTML and CSS. We invite you to begin the tutorials right away. We have... * A Beginner tutorial - For those just starting to learn to make web pages. * HTML Tutorial - Begin your web designing with a solid background in HTML. * CSS Tutorial - Check out the latest web design techniques available to you. * PHP Tutorial - Understand what all the PHP hype is about with our tutorial. * Web Host Guide - An overview of all the information you need to know about choosing and using a web host. * CSS Reference - CSS Quick-Reference sheet. Each item of the reference also has an accompanying example. * HTML Reference - HTML Tag Reference including attributes associated with each tag and accompanying examples. This site is dedicated to all the researchers and reverse engineers interested in Reverse Code Engineering (RCE) techniques and practices and all things related. You will be able to find a wide breadth of information retained on this site to help in your research ranging from; anti-debugging, virtual machines, unpacking, coding, disassembling, debugging, keygenning, cryptography and much, much more.
This site is dedicated to all the researchers and reverse engineers interested in Reverse Code Engineering (RCE) techniques and practices and all things related. You will be able to find a wide breadth of information retained on this site to help in your research ranging from; anti-debugging, virtual machines, unpacking, coding, disassembling, debugging, keygenning, cryptography and much, much more. Vim is a highly configurable text editor built to enable efficient text editing. It is an improved version of the vi editor distributed with most UNIX systems. Vim is often called a "programmer's editor," and so useful for programming that many consider it an entire IDE. It's not just for programmers, though. Vim is perfect for all kinds of text editing, from composing email to editing configuration files.
Vim is a highly configurable text editor built to enable efficient text editing. It is an improved version of the vi editor distributed with most UNIX systems. Vim is often called a "programmer's editor," and so useful for programming that many consider it an entire IDE. It's not just for programmers, though. Vim is perfect for all kinds of text editing, from composing email to editing configuration files. At W3Schools you will find all the Web-building tutorials you need, from basic HTML and XHTML to advanced XML, SQL, Database, Multimedia and WAP, Totally Free. Great for people new to computer languages.
At W3Schools you will find all the Web-building tutorials you need, from basic HTML and XHTML to advanced XML, SQL, Database, Multimedia and WAP, Totally Free. Great for people new to computer languages. Web Application Attack and Audit Framework. W3af is a great piece of software designed for testing web applications. Written in Python. Comes with over 100 plugins for brute-forcing, evasion, page discovery, exploit discovery and exploits. Extensible with Python.
Web Application Attack and Audit Framework. W3af is a great piece of software designed for testing web applications. Written in Python. Comes with over 100 plugins for brute-forcing, evasion, page discovery, exploit discovery and exploits. Extensible with Python. WebGoat is a deliberately insecure J2EE web application maintained by OWASP designed to teach web application security lessons. In each lesson, users must demonstrate their understanding of a security issue by exploiting a real vulnerability in the WebGoat application. For example, in one of the lessons the user must use SQL injection to steal fake credit card numbers. The application is a realistic teaching environment, providing users with hints and code to further explain the lesson.
WebGoat is a deliberately insecure J2EE web application maintained by OWASP designed to teach web application security lessons. In each lesson, users must demonstrate their understanding of a security issue by exploiting a real vulnerability in the WebGoat application. For example, in one of the lessons the user must use SQL injection to steal fake credit card numbers. The application is a realistic teaching environment, providing users with hints and code to further explain the lesson. WhatWeb is a next generation web scanner that identifies what websites are running. Flexible plugin architecture with over 80 plugins so far. Passive plugins use information in the headers, cookies, HTML body and URL. Aggressive plugins can identify versions of Joomla, phpBB, etc by making extra requests to the webserver
WhatWeb is a next generation web scanner that identifies what websites are running. Flexible plugin architecture with over 80 plugins so far. Passive plugins use information in the headers, cookies, HTML body and URL. Aggressive plugins can identify versions of Joomla, phpBB, etc by making extra requests to the webserver XVI32 is a freeware hex editor running under Windows 95, Windows 98, Windows NT, Windows 2000, and Windows XP.
XVI32 is a freeware hex editor running under Windows 95, Windows 98, Windows NT, Windows 2000, and Windows XP. This site offers a collection of tutorials, articles, and programs useful for people interested in programing, system administration, and web design for Windows, Mac, or Linux.
This site offers a collection of tutorials, articles, and programs useful for people interested in programing, system administration, and web design for Windows, Mac, or Linux.














